Extract Widevine L3 CDM from Android with Dumper
🔓 How to Dump Widevine L3 CDMs from Android Devices – Full Tutorial
This guide explains how to extract Widevine L3 CDM (Content Decryption Module) files from Android devices using Dumper, an open-source tool based on Frida.
Extracting your own CDM enables testing of DRM-protected content in environments like Pywidevine, offline decryption, or stream analysis tools.
⚠️ For educational and research purposes only. Do not use this method to violate DRM protections or distribution agreements.
🧰 Requirements & Dependencies
You will need:
- An Android device (with Widevine L3 support)
- ADB & USB debugging enabled
- Frida installed on both PC and Android
- Python 3 (tested with 3.7+)
Clone the Dumper tool from GitHub:
git clone https://github.com/wvdumper/dumper
cd dumper
pip3 install -r requirements.txt
⚙️ Step-by-Step Guide
1️⃣ Enable USB Debugging
On your Android device:
- Go to Settings > About Phone > Tap Build Number 7x to enable Developer Mode
- Then go to Developer Options and enable USB Debugging
2️⃣ Start Frida-Server on Android
- Download a compatible
frida-serverbinary for your device’s architecture - Push it to your phone:
adb push frida-server /data/local/tmp/
adb shell "chmod 755 /data/local/tmp/frida-server"
- Start the server:
adb shell "/data/local/tmp/frida-server &"
3️⃣ Launch the Dumper
On your PC, run the script while the device is connected:
python3 dump_keys.py
Keep this terminal open!
4️⃣ Start DRM Playback on the Device
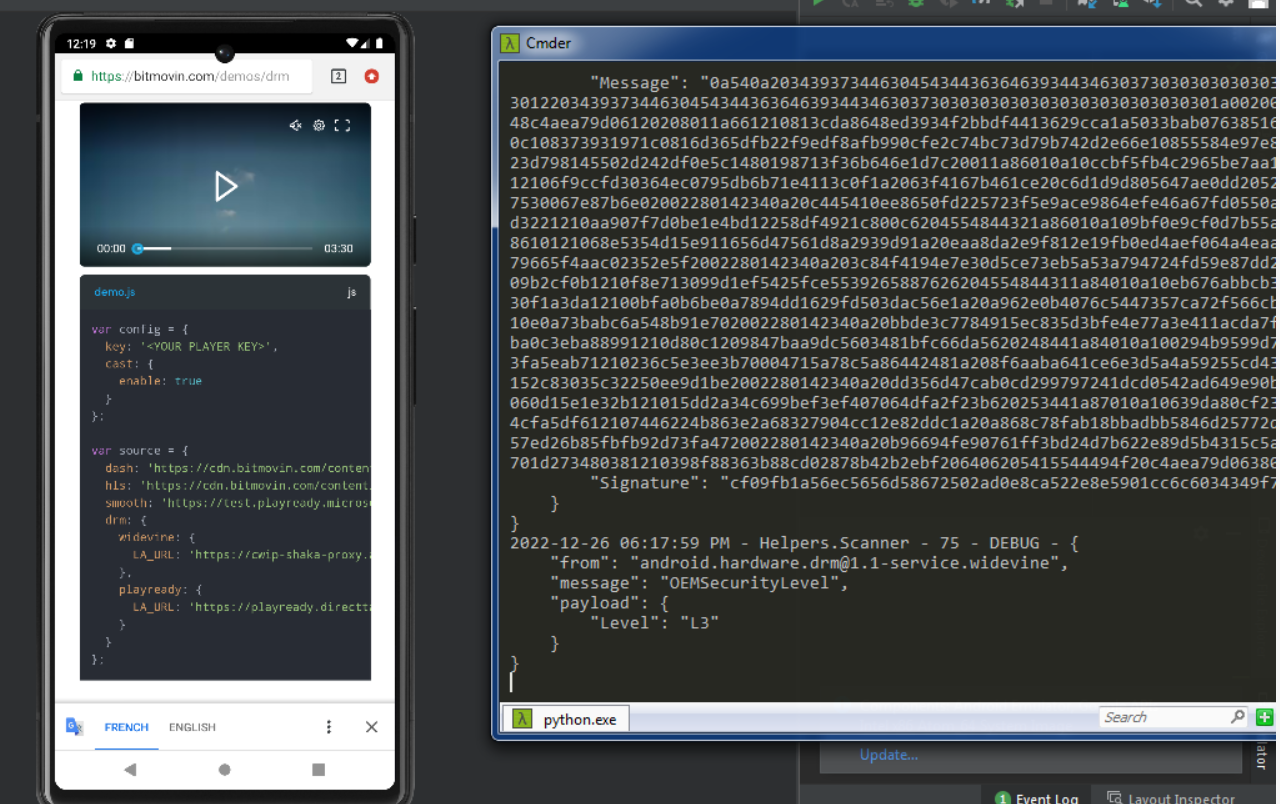
Go to a DRM-protected video using a browser like Chrome (e.g. Bitmovin demo page) or a streaming app.

Once the video starts playing, the Dumper script will extract the required Widevine data.
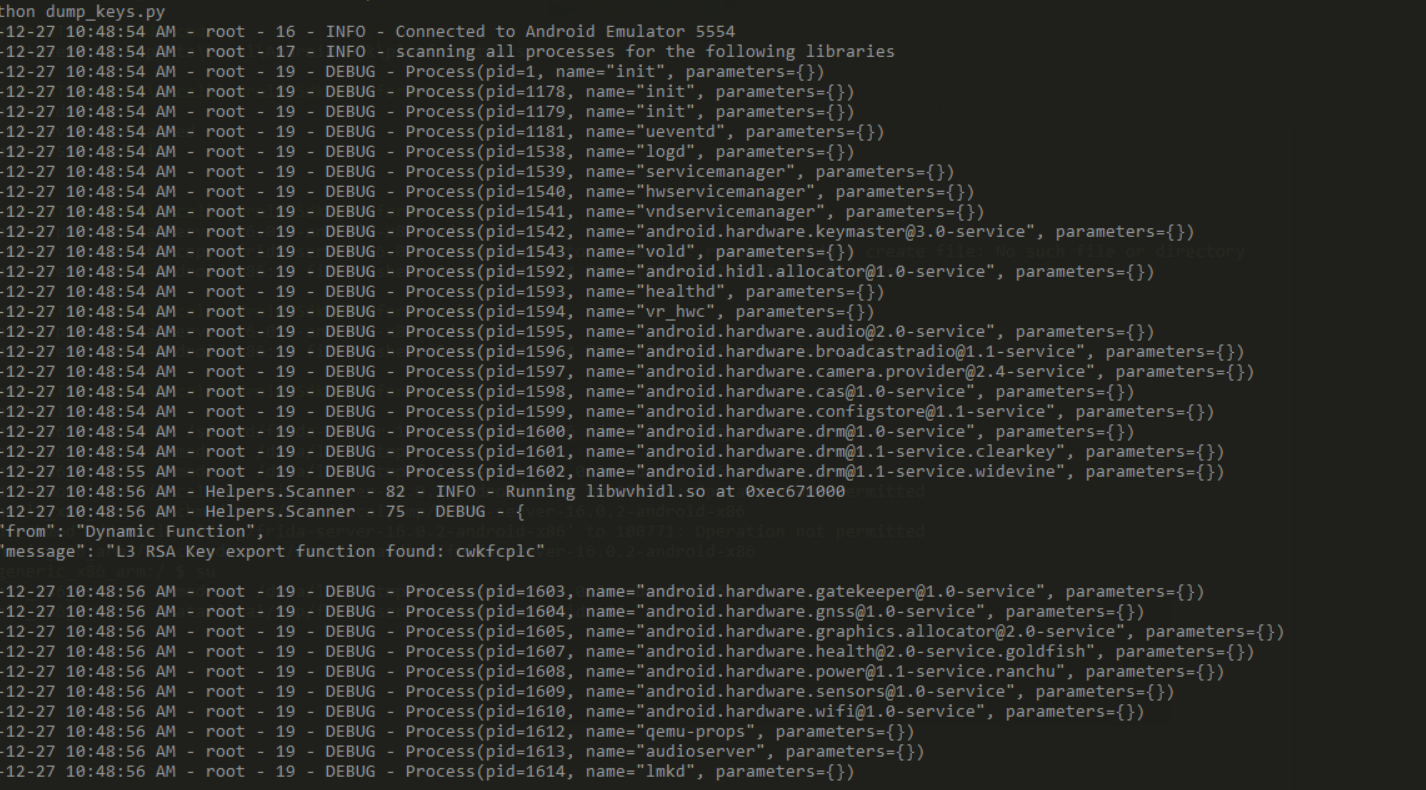
🔐 Temporary Disablement of L1 to Force L3
Some brands (like Xiaomi) may default to Widevine L1, which is not accessible after bootloader unlock.
To force L3, install the Magisk module:
- Module name:
liboemcrypto-disabler - Install via Magisk Manager
- Reboot
Now, Widevine will fall back to L3 and Dumper will work.
📦 Output Files You Will Get
After Dumper completes, you’ll find a new directory called private-keys containing:
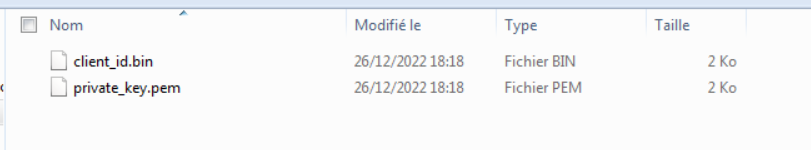
client_id.bin→ rename todevice_client_id_blobprivate_key.pem→ rename todevice_private_key
These files are essential for:
pywidevinewidevine_keyso11 OTT Streamer- Custom DRM testing tools
🔍 What is a Widevine L3 CDM?
A Content Decryption Module (CDM) is the secure core of any DRM system. It handles:
- License requests
- Secure key management
- On-device decryption of media content
Widevine L3 is a software-based CDM level:
- Runs entirely in user space
- Does not require Trusted Execution Environment (TEE)
- Easier to extract & analyze for testing and automation
Once extracted, an L3 CDM can be used to:
- Request Widevine licenses programmatically
- Extract decryption keys from license responses
- Use tools like Pywidevine, widevine_keys, or WKS-KEYS
- Build Python scripts for auto-updating keys and tokens
- Test browser extensions that interact with EME APIs
- Integrate with o11 OTT Streamer or Xaccel-Codec
CDMs are critical components for any DRM decryption workflow. Having your own L3 CDM gives you full control over testing, automation, and research.
🔗 Use Your CDM in Pywidevine
Once you have your CDM files, you can use them with Pywidevine to:
- Send license requests
- Parse MPD + PSSH
- Extract decryption keys
- Decrypt video segments offline
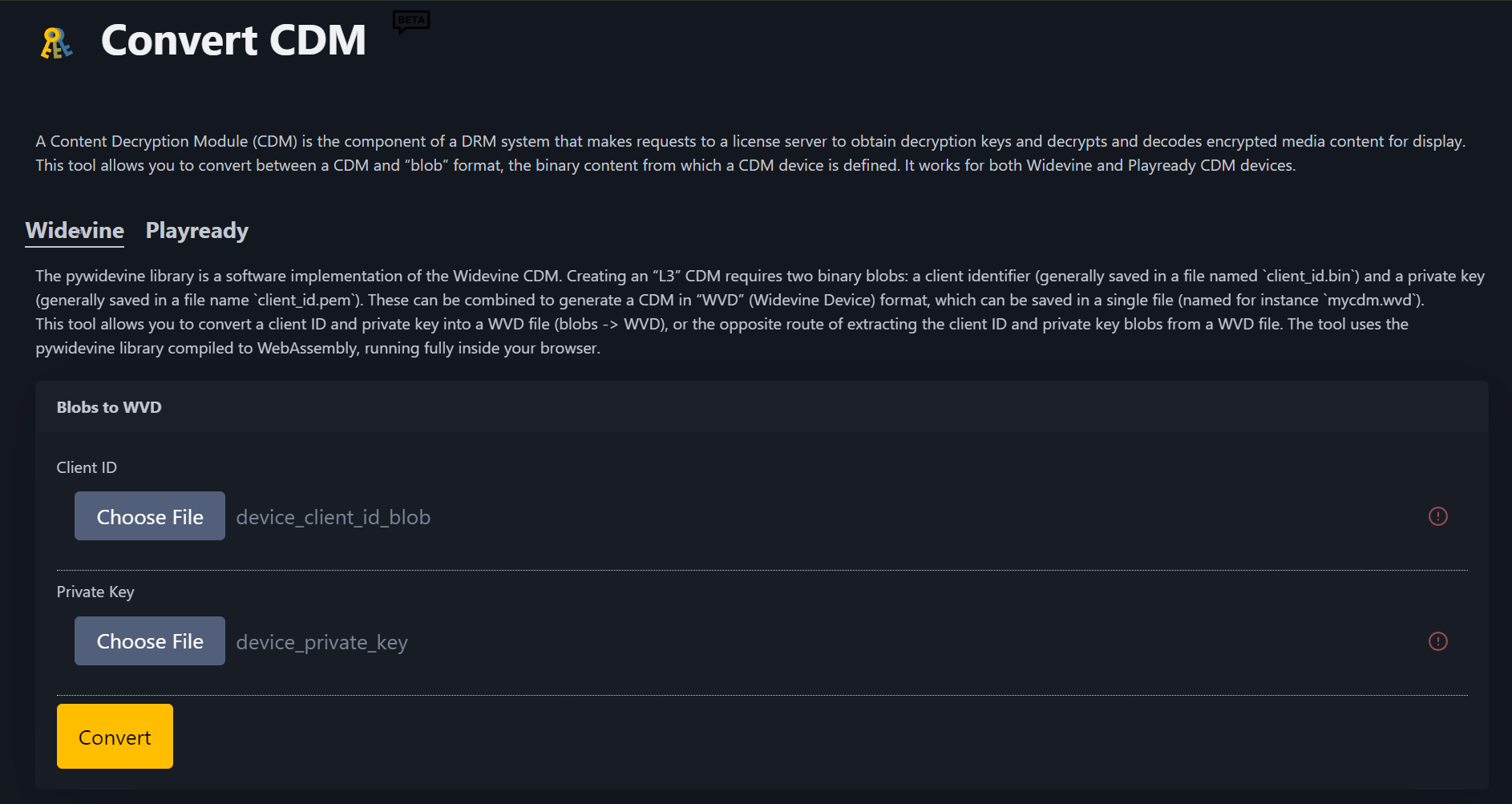
🔁 Convert Blobs to WVD Format (or vice versa)
If you want to convert your extracted CDM blobs (device_client_id_blob and device_private_key) into a .wvd file (Widevine Device file), or extract blobs from a .wvd, you can use this browser-based tool:
This tool runs fully in the browser using WebAssembly compiled from Pywidevine. It supports both Widevine and PlayReady formats.
▶️ Modes Supported:
- Blobs → WVD: Combine
device_client_id_blob+device_private_keyintomycdm.wvd - WVD → Blobs: Extract individual components from a
.wvdfile
No server-side processing, 100% client-side and safe for local use.
📌 Final Notes
- Dumper works only on devices running L3, or where L1 is bypassed
- This method is ideal for security researchers, DRM engineers, and testers
- Never share extracted CDMs publicly – treat them as private credentials
🔗 Source Project: https://github.com/wvdumper/dumper
🔗 Source Project: https://emarsden.github.io/pssh-box-wasm/convert

Want to test your CDM with our tools? Visit → https://iptvtools.io/drm-tools/


